Asahi ran out of beer 🍺 because of... hackers
Season 10, Issue 2: Crisis comms, cyber attacks, and data leaks
📫In this issue:
Breaking down comms from Asahi, Qantas, and Dymocks
You can’t own the narrative, but you can own the brand sentiment
Best practice for breaking bad news
Hola Mehketeer,
Cyber attacks and data breaches usually makes pretty big news, so I was surprised when the Asahi breach was pretty well contained to niche corners of the (English) internet and Japanese media.
Some quick context:
In case you missed it, the summary of the news is that Asahi Group Holdings was hit by a cyber attack, contained to Japan, which shut and/or affected a number of their operational systems that impacted their beer supply. Asahi is the largest brewer in Japan, with a 37% market share (interestingly, it’s got 48.5% of the Australian beer market.)
Japan is famous for their nama beer which is unpasteurised, giving it a shorter shelf life and quicker stock turnover. The interruption to Asahi’s systems mainly affected their ability to receive and fulfil orders, so instead of continuing to produce the beer and have it sit on a shelf, they decided to halt production. This halt and system interruption placed a lot of uncertainty on the supply.
Would the beer run out before production resumed? Would the beer run out and force restaurants and bars to switch to a different beer supplier?
Let’s find out how they handled this!
Asahi’s crisis comms
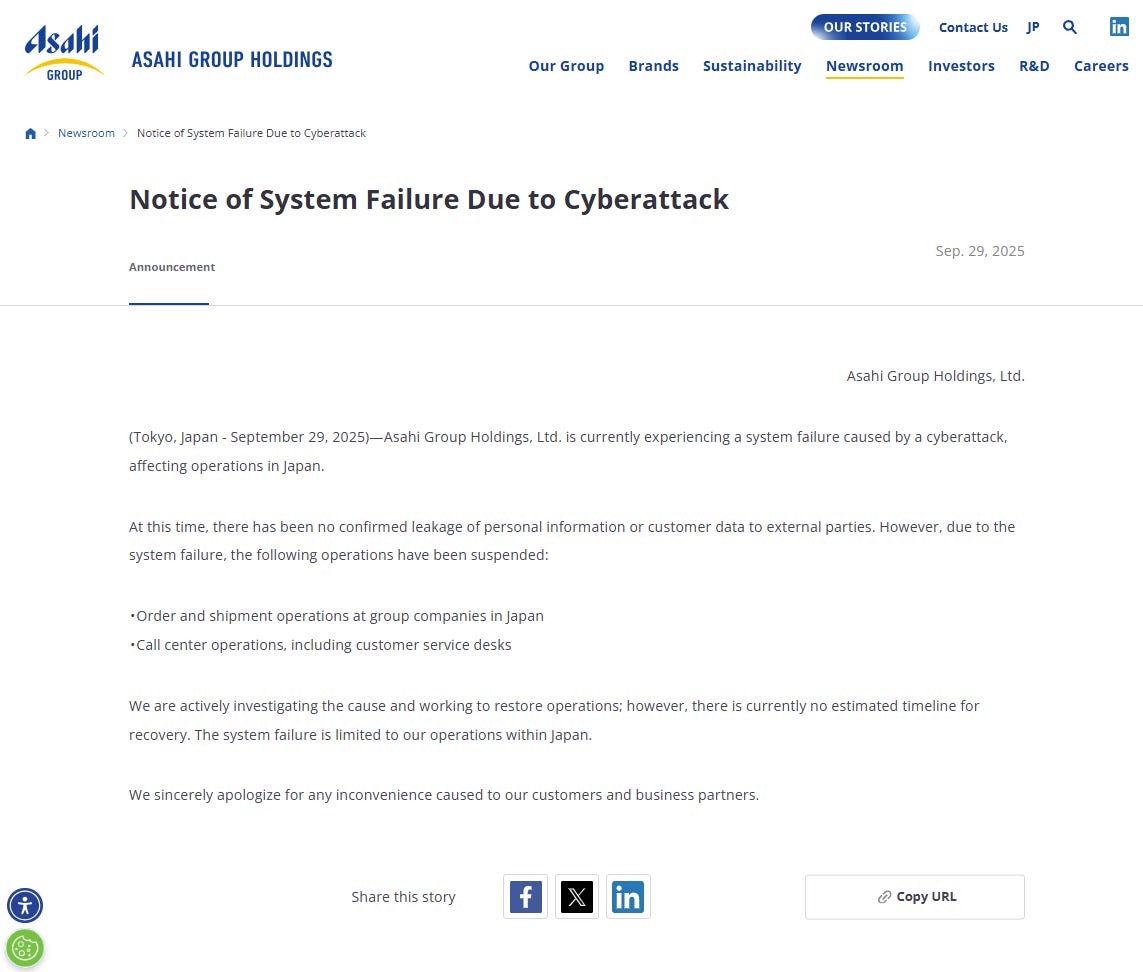
The very first announcement from Asahi, in full (Sept 29, 2025):
(Tokyo, Japan - September 29, 2025)—Asahi Group Holdings, Ltd. is currently experiencing a system failure caused by a cyberattack, affecting operations in Japan.
At this time, there has been no confirmed leakage of personal information or customer data to external parties. However, due to the system failure, the following operations have been suspended:
Order and shipment operations at group companies in Japan
Call center operations, including customer service desks
We are actively investigating the cause and working to restore operations; however, there is currently no estimated timeline for recovery. The system failure is limited to our operations within Japan.
We sincerely apologize for any inconvenience caused to our customers and business partners.
I was so surprised by how short and lacking in information this is. Understandably, maybe they didn’t have a lot of factual information at this time, but there’s still such a gaping hole in messaging.
We’ll see some examples of what this could have been further down. Let’s continue with the Asahi announcements:
Here’s an excerpt from the second announcement on October 3:
We took immediate action to contain and respond to the incident. We placed the highest priority on safeguarding critical data, including the personal information of our customers and business partners, and promptly isolated the affected systems to minimize the impact.
Subsequent investigations have confirmed traces suggesting a potential unauthorized transfer of data. We are conducting investigation to determine the nature and scope of the information that may have been subject to unauthorized transfer.
This was followed up by a third announcement on October 8, which includes the line “investigations have confirmed that data suspected to have been subject to unauthorized transfer as a result of the recent attack has been identified on the internet.” They also note that production resumed on October 2nd in all domestic factories, and shipments had partially resumed.
It sticks out to me that production resumed on the 2nd, they had an update on the 3rd that didn’t mention it, and they didn’t announce it until the 8th.
On October 14, they posted two notices to their site. The first was an announcement that they would be postponing their disclosure of financial results for Q3, and the second was an official update on the cyber incident.
The second post was an update on the cyber incident and included “we have identified the possibility that personal information may have been subject to unauthorized data transfer.”
Disclaimer: This post was written on October 19, so any updates that have been sent since then weren’t included in this analysis.
Information in press coverage not in the Asahi announcements
An official update on a company newsroom post is one source of information, but it’s not the only one. Spokespeople giving interviews and answering press releases is another source, but of course journalists are the embodiment of this meme:
The BBC dug through Asahi’s previous reports to find this nugget:
In a report last year, Asahi listed a cyber-attack as among the main risks it faced in the medium to short term.
It assessed that such an attack could potentially lead to an interruption of its business, create cashflow issues, and damage its brand.
The Register reported on the other side of this attack, the hackers claiming ownership of it:
The attack was claimed by the Qilin ransomware crew, which has boasted of stealing around 27 GB of files, including contracts, forecasts, employee records, and financial data. Samples of the allegedly stolen data, seen by The Register, suggest Asahi’s fears of personal data theft are well-founded, with Qilin posting what appear to be employee ID cards and other personal documents.
All this is to say — you don’t get to own the narrative in a crisis.
What could Asahi have done better? A look at Dymocks and Qantas
Dymocks 2023:
The Dymocks breach happened in 2023, and is, in my opinion, the best response we’ve seen to a data breach. They still have an FAQ on their newsroom about the breach.
I’ve got three emails from them in the depths of my inbox, the first one opens with:
We have become aware that some of our customer information may have been compromised. We are still investigating this but we wanted to be proactive and warn you that there is a chance that this has occurred. For now, we advise you to be vigilant and monitor your accounts for any unauthorised activity, and as a precaution change your password.
It then has a detailed breakdown into what steps they have taken since detecting the breach (~two days before the email was sent), what kind of information was impacted, what steps individuals can take, and what support Dymocks is offering to customers.
One of the simplest things this email did was list resources for self-educating on scams, including linking to government websites and resources. They highlight the importance of taking precautionary steps to protect yourself as something to do regularly, not just when a breach happens.
Qantas:
In July of this year (2025), Qantas had a breach that affected different customers to varying levels.
There’s three things that I want to point out:
They staggered and personalised their customer comms. I got off pretty light, my name, Frequent Flyer number, and status tier were compromised, however friends who had more data leaked told me they received emails later than I did, with the longer list of exposed details.
Like Dymocks, they included “What steps can I take to protect myself?” and “Support available” segments in their comms.
As noted in this piece from Capital Brief, “Just three years ago, large-scale cyber attacks often meant a chief executive’s job was on the line. Now it simply means wrapping up a family tour of the Greek islands early.” — Qantas handled this well enough that it was kind of a “eh, whatever” hack.
The lesson: Being helpful, even if you’re not informative, goes a long way in terms of brand sentiment
Both Dymocks and Qantas avoided huge blowback on this. When looking at the press headlines, Asahi gets vocabulary choices like “Asahi admits” which is 1. active voice and 2. has the connotation of trying to hide it at first.
A cursory search for Qantas and Dymocks headlines shows the active voice is mostly used when referring to the hackers (“Hackers leak Qantas data”, “Hackers release customers’ data”)
Bad news best practice
Earlier this year I did the AICD Foundations for Board Directors course (highly recommend, btw) and part of it was a crisis role play. The scenario my group was given was the sudden death of the CEO while the company was in financial uncertainty. It was really interesting the way the facilitator was able to point out ways our press release could be interepreted in so many ways.
Public companys have the pressure of a statement potentially negatively impacting their share price. What’s damning for Asahi is that a public report named a cyber attack as a threat, and they didn’t reference that in their announcement. To me, it’s possible to interpret this as “we have taken no action, despite identifying the threat.”
A very simple “cyber attacks are a known threat to Asahi and we are following our procedure accordingly” could have covered this off.
So here are my best practice principles:
State the facts
Acknowledge responsibility, actions already taken, and immediate plans
Provide helpful educational resources, even if they’re not from your organisation
Set expectations on milestones that will trigger future comms, for example at the completion of an investigation
A personalised message from the CEO wouldn’t go astray, but don’t say too much
Advice from an actual PR, Harrison Polites
Harrison is genuinely my PR fairy godmother, and I asked him to read over this and point out anything I forgot. Here’s his take:
Crisis workshops and exercises (both internal and external) tend to assume you have all the facts when dictating a response. From personal experience, this is seldom true, especially with smaller companies. Founders tend to embellish as its their personal reputation on the line. Some of the crisises where I’ve personally fudged the response in the past have come from not knowing all the all the facts before approaching media, or through the exec sugar-coating them to me. Simply put: When the media know more than your PR, you are in for a bad time.
Understand the difference between a crisis and bad media. One bad story is not a crisis… When multiple news outlets are all seeking comment from you on deadline, that’s a crisis. It can take experience however to identify those incidents where what starts as a simple story will trigger a full-blown crisis. A good indicator: If it involves the courts, government or a regulator, it’s likely a crisis.
Know when to scale-up your support. For emerging brands, in most instances, your retained PR is enough. If you in-house marketer has PR experience, that may be enough too. Especially if it’s only one story. However, during a proper full-blown crisis, you may need a dedicated PR resources, tailored to managing these incidents.
Do your best. There’s always internal hurdles or mitigating factors that the public won’t see. On the assumption you have no help or support, the advice Kayla’s offer here is sound. Be clear, be quick and be reasonable. Journalists have a job: They can do it here with or without you. Remember: In a genuine crisis, a lack of comment will not kill the story. The reporter will just write that you declined to comment.
Thanks Harry! If you need him, here’s his LinkedIn. And here’s his Substack where he writes about gaming!
This Mehdeeka comes to you from Japan
That’s right, I’m in the land of magnificent train advertising. Have a read of why it’s so good here:
Will I find new amazing advertising in Japan on this trip? Probably! Join the Mehdeeka chat on Substack, I’ll post photos of interesting ads and formats I find.
That’s it for now,
じゃあ、また!
ケイラ







I didn't check announcements in Japanese (they'd likely be the original versions of these announcements with the English being a direct translation)
I looked up some articles in Japanese about it where it was interviewing restaurant/bar owners about whether or not they'd be switching to a different beer ahead of Asahi running out to avoid business interruptions, but overall decided to just focus on the English comms available. It was overall pretty underreported in English since it didn't impact regions outside Japan which is also why it was kinda weird that the English reporting went so hard on it!
It's interesting how you framed the whole Asahi situation; your breakdown of their crisis comms strategy is really insightful. I do wonder though, if the news being so contained wasnt also partly because of the specific attack vectors or perhaps just lucky timing in the broader news cycle. Still, a fascinating anlaysis.